So when we are talking about cybersecurity a lot of people says the following things: CIA triad, Threat modelling, securing OSI or TCP layers, but as a newbie, these things didn’t help me too much…
The problem with a lot of courses, youtube videos and boot camps is that they are specializing in one or two topics which they explain so you can understand them, but you can’t see this specific topic, technology or solution on the whole. The way of studying cyber should be learning topics, solutions, and vulnerabilities and trying to see them as an entire system.
One thing that helped me a lot in understanding the methodology, the techniques and the industrial solutions is the On-Premises Information Systems Architecture model. On-premises means on-site and I learned about it when I was learning cloud. In today’s post, I want to show this model and secure an imaginary network with you!
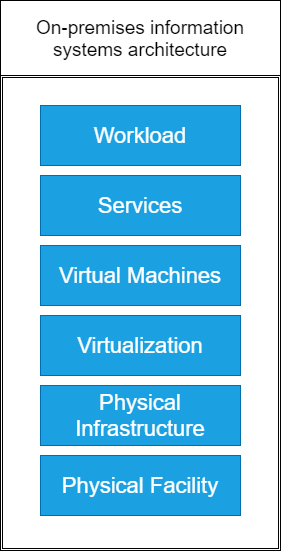
From the bottom, up we have the Physical Facility, which is the actual building with the machinery, cooling…etc, where our systems are located, it can be a warehouse, an office or an actual plant.
How do we secure this? Imagine that you have a house full of gold, what security measures would you apply? A fence, video surveillance, electronic locks, two-factor authentication, security personnel and we can apply many more things.
Moving on we have the Physical Infrastructure, which means both our hardware and software on this level: servers, cables, PCs, access points, PLCs…etc.Here we have our operating systems and firmware also.
Let’s ask the question again. How do we secure this? First things first, we have to have every system up to date. When I say every I mean every system, from operating systems to the firmware. Then before connecting to the Internet we have to set up a Firewall. Then segment the network, let’s say for 4 segments: servers, PCs, wireless, and one for the industrial systems and their operators.
Between every segment we can implement a firewall, we can implement (and should) a SIEM solution a sandbox solution, and many more things. But with a properly segmented network, with some well-configured firewalls and a SIEM solution, our imaginary network should be good.
At the Virtualization level, we have the virtualization software which normally is VMware or Hyper-V. This is our virtualization platform and its needs to be maintained (up to date) and licensed. This is the only important thing at the moment for us.
Virtual machines are like regular PCs, you have to update to OS, and the software you use on it, these are our everyday windows and Linux systems.
Services can be everything you use in an industrial environment, MongoDB for database services, SSH for secure shell connection, IMAP for email services, Active Directory and a lot more. We are gonna come back here in a moment.
Workload means any program that runs on a computer or the work done by it. Like an SAP query, analyze a bunch of data, HTTP requests to a web server.
Let’s get back to services, it’s a huge topic and I can’t show everything in one simple post but I can teach you some things.Some norms you have to follow always:
1. Change the default credentials/disable anonymous login.
2. Use encryption always to prevent traffic sniffing/modification.
3. Enforce strong passwords for your users.
4. Use 2-factor authentication.
To give you an example let’s try to secure a regular FTP service. What you can do with it?
1. Disable it, it’s like a 30 years technology :D. Use FTPS or SFTP instead (look below).
2. Use SFTP (FTP over SSL).
3. Change the default port from 21 to something else.
4. Change the admin username from admin or root to something else.
5. Enforce strong passwords.
6. Implement IP Blacklists and Whitelists
7. Use good account management, and assign the fewer rights possible.
8. Encrypt files which are not in use/don’t store sensitive on the FTP server.
9. Use Elliptic curve Diffie-Hellman key exchange algorithms
By encrypting the traffic via SSL, encrypting unused files and using Diffie-Hellman key exchange algorithms we can maintain the integrity and confidentiality of the data. Sounds familiar? 🙂
Cybersecurity is a huge field, I highly suggest you do your research on topics like Hardening, Securing the perimeter, and Firewall configurations. As I said I can’t show everything in a post but I hope I give some general understanding. Make your own model and after learning every vulnerability, solution or technique try to find its place in your model.





