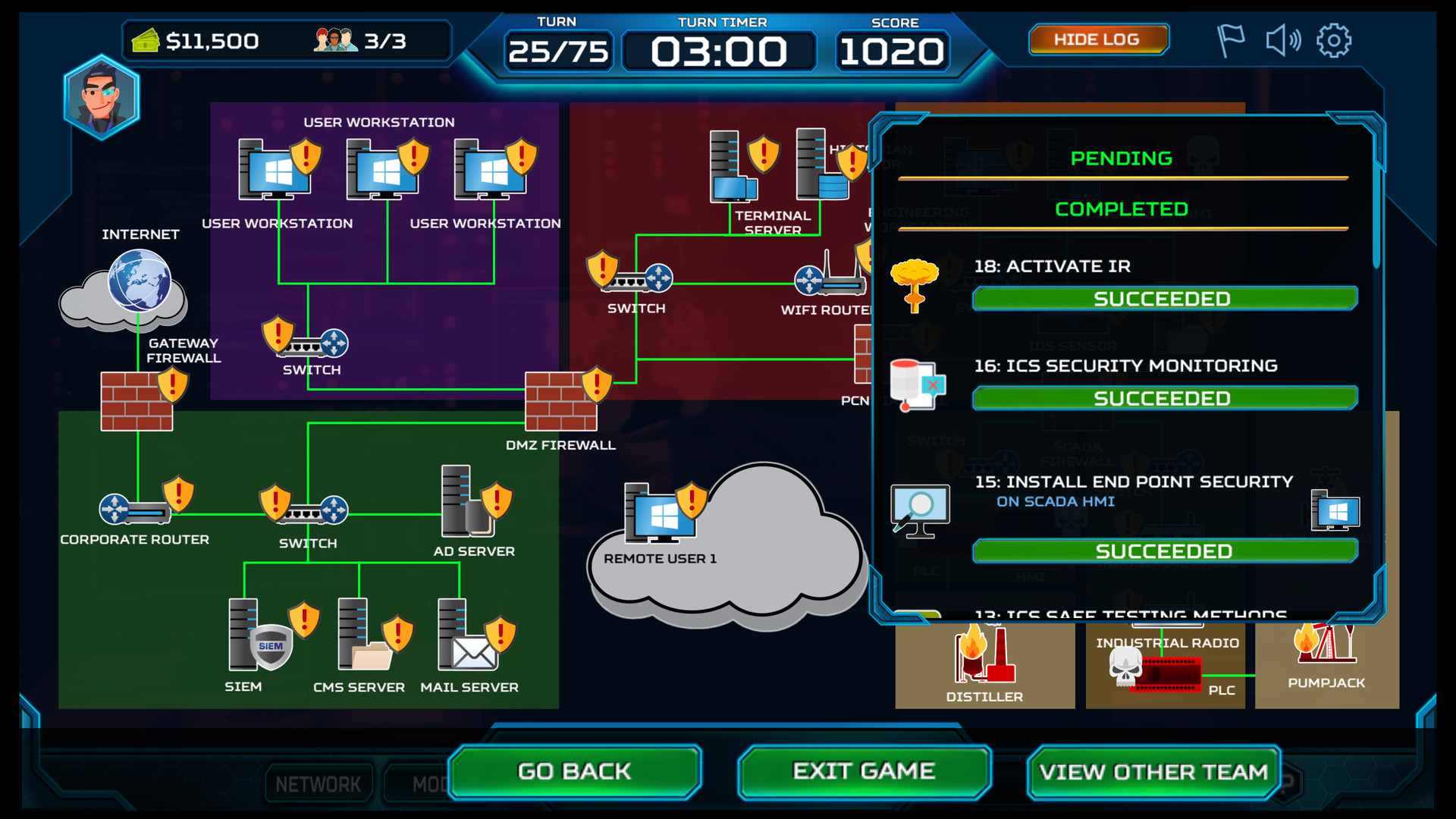
Hey guys, today I realized that I have almost 80 hours in this game, and I saw a lot of people who also want to give it a go, but don’t know where to start. So in this post, I will try to show you some of the basics of this game.
Let’s start at the beginning: What is ThreatGEN: RvB? It is a turn-based strategy game which helps you learn cybersecurity, whether you are a beginner or a professional, whether you are more of a blue team person than a red team one. Amazingly, you don’t need technical knowledge or command-line skills to play it. It has an amazing GUI, where at first sight you are a little bit lost, but with some practice, it becomes crystal clear what you have to do.
During regular gameplay, try to apply what you know about the cyber kill chain or security frameworks and use a lot of common sense. Also, give yourself time, because this game is huge, with a lot of actions, a lot of attacks and counters. I needed at least 3 games to figure out the basics and another 5 to fully understand the game. Be patient and give yourself time, because this game will reward it.
THE OBJECTIVE
Very simple, as the Blue Team (BT) you can do the following to win:
- Survive 75 rounds on default settings
- Patch up every vulnerability within your network (never did it)
- Win by Threat Intel
The first two are pretty obvious, but let’s see what the third one means.
While playing as BT you will have a Threat Intel and a Profit/Loss meter at the top of the screen. The Threat Intel grows when you play the gather forensics action, detect an on-going attack (by installing an IDS sensor on the subnet where the attack action was played by the red team), detect a compromise or denial, or detect Red Team’s activity on the perimeter or onsite.
How can you lose as BT and how can you win as Red Team (RT):
- Bring down the Profit/Loss meter to 0% for BT
- Damage the ICS process
To bring down the Profit/Loss meter you have a ton of options:
- Install and activate ransomware on compromised assets
- Install distruptive malware
- Exfiltrate data
- Deny assets
You have more options as well, but these are the ones which are gonna help you bring down the P/L meter.
Exfiltrating data is a one-time playable action on each compromised asset and you need 2 resources for it.
You can install ransomware for 2 resources as well. Also, after installing it you have to activate it which requires 0 resources but 1 turn.
When you install disruptive malware, BT can only detect it by looking at their P/L meter.
After every turn, if the P/L meter goes down a little for BT if they have a ransomed asset or an asset with disruptive malware.
Denying assets: You can research vulnerabilities and instead of going for manipulation, you can try to deny the assets. Denial attacks tend to be more successful, as in real life triggering a buffer overflow on a firewall or a web app is way easier than using it to compromise the asset.
If you compromise a PLC (Programmable Logic Controller, mainly used to manage processes in industrial systems, it is connected to sensors and can control ventilation, pressure in pipes, etc.) you can go for the Damage ICS Process action which takes 5 resources and takes 1 turn, but can instantly win the game for you.
To win as RT, you can either go for the crown jewels (PLCs), fight your way through the firewalls between every subnet or compromise as many assets as possible and try to bring down the P/L meter for the Blue Team (but be careful, if BT detects your compromises, they can clean them and grow their Threat Intel!)
Now let’s see the interface itself
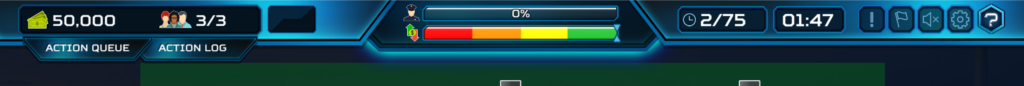
At the top of the screen as BT,you can see your budget and resources, in the middle the Threat Intel and your Profit/Loss meter and next to them the actual turn of the game, a timer, notifications, a flag to hide and show the names of the assets, a button for mute, options, and at the end a help menu. I highly encourage you to use it a lot at the beginning!
Most actions as BT require some budget and resources, some actions can also take more than one turn.
If the P/L meter goes down to 0%, you lose, if the Threat Intel goes up to 100%, you win.
After you detect a compromise the game sends you a notification, you can check them in the notification menu.
At the top left, we have the Action Queue where you can see the actions you want to play before the turn ends, next to them there is the Action Log, which shows played and on-going actions.
The rest of the things do not require an explanation, let’s move on!
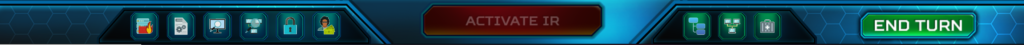
On the bottom, you can see the Action Toolbar where you can play your actions, in the middle, there is a big red Activate IR button which we don’t like to push either in the game or IRL, next to it there are the view modes: action tree, network view, mode view. At the end, there is the end turn button, after selecting your actions make sure to push it so the game can continue.
From the action toolbar, you can choose the type of action you want to play, like segmenting the network, installing sensors, asking the management for more money, etc.
Activating IR mode lets you clean assets, gather forensics, and threat hunt, but you can’t patch up systems. As IRL when we detect a ransomware infection we don’t start to patch up systems, we start to isolate infected assets, gather forensics and clean them. To do these actions first you have to play the Create IR procedures action from the Threat Monitoring option.
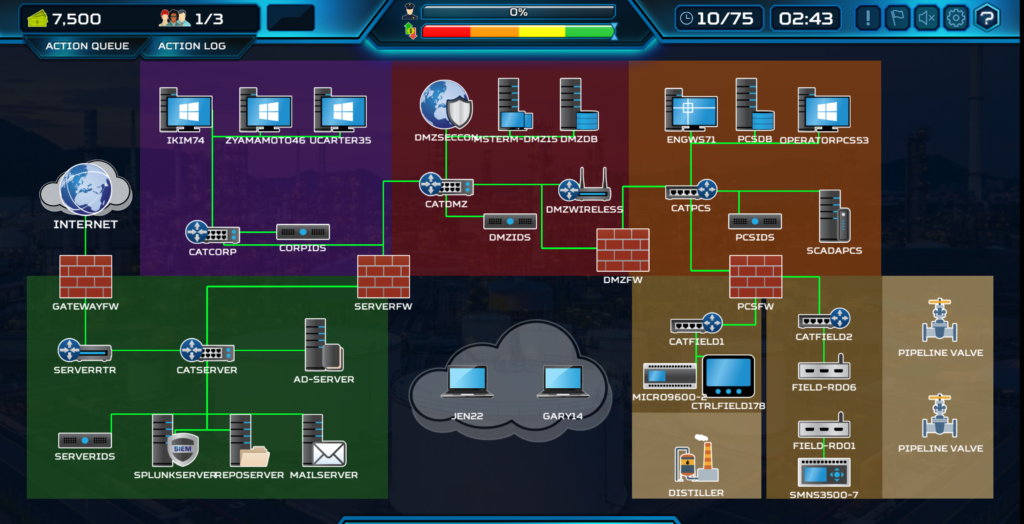
This is a snapshot from the early game, where I already installed some sensors, segmented the network and installed VPN. Explaining every asset would require a lot of time and this post is already long enough so I recommend you to some practice rounds against the AI and click around to know more about them.
Your most important assets are the devices which are open to the Internet, your VPN (DMZSECCOM), your main firewall (GATEWAYFIREWALL), and SIEM (SPLUNKSERVER).
If you want the red team out of your network, you should patch up this asset first. The SIEM is one of the most important assets of BT, the compromise of this system results in complete blindness of your network, you will not able to see compromises.
This was a general overview of the game itself to give you some idea about the interface and the objectives of each team. In the next post, we will see how the red team can achieve its goals and win the game!
For more information i recommend you the visit the official website of ThreatGEN:
If you have any questions about the game or you are searching for somebody to play with check out their Discord server: