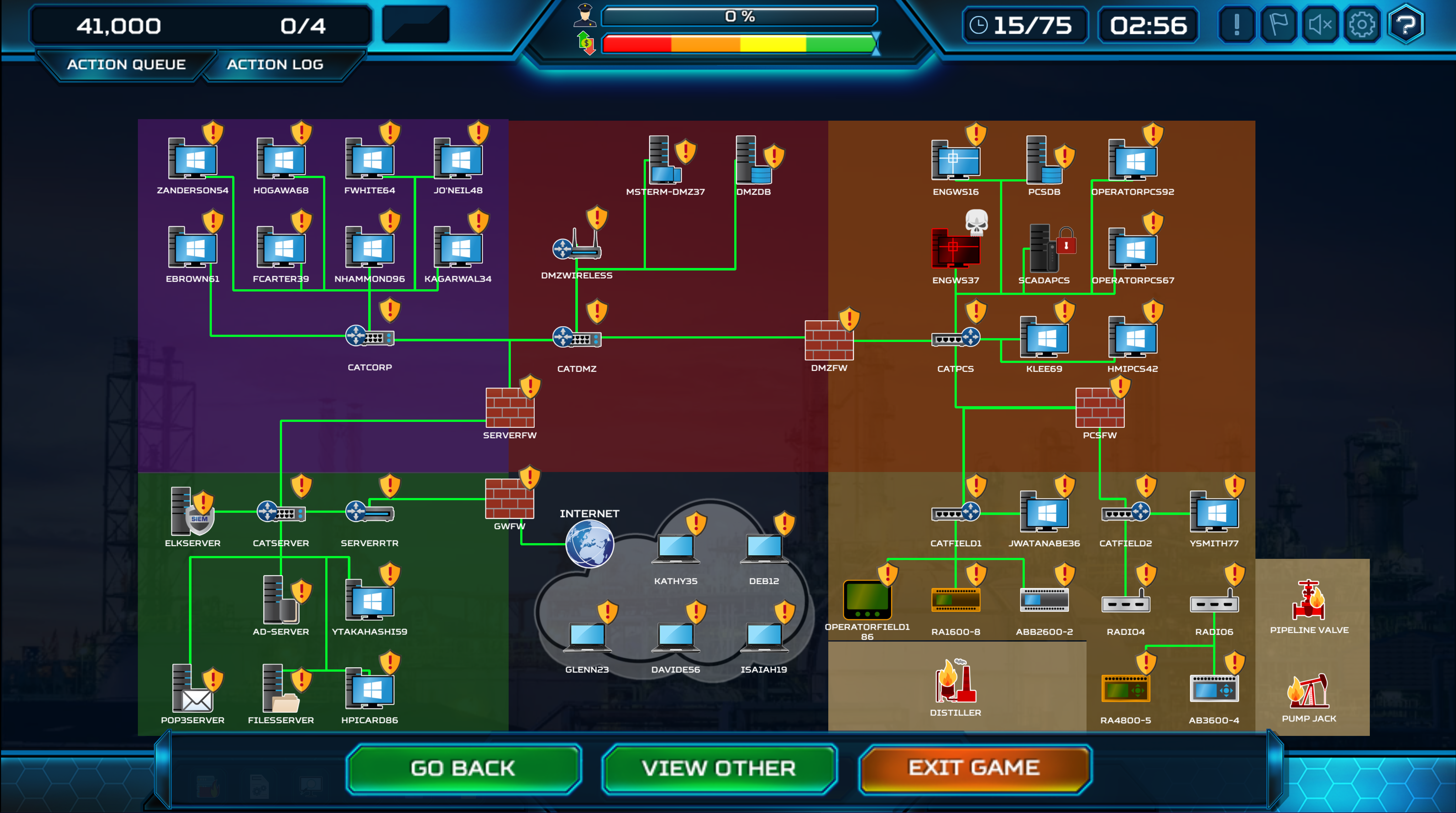
Check out the previous two posts so this one gonna make much more sense to you!
ThreatGEN RvB red team tactics
So we saw the basics and some red team tactics to win the game, now we are gonna switch sides and see how can we counter the different tactics of the blue team. As a blue teamer, we cant patch up everything so we have to focus our resources on where the attack might happen. In this, our objective is to find out which tactic to red team gonna use and act accordingly to counter it.
If a red team goes with the “HMI Search Cheese” tactic then instead of putting all of our resources into the safety of our infrastructure we should focus on physical security. Install video surveillance should be played in the first turn, and then you might install electronic locks as well. These two actions can counter this tactic fairly well. After the red team got kicked out, it gives you some threat intel and makes their way back a lot harder because of the installed cameras. You can also go full throttle on physical security and install physical 2FA (2-factor authentication) to get the fort knox achievement but in my experience, the first two actions should be enough.
- Turn 1: Gateway Firewall, Install video surveillance, Install electronic locks, Asset inventory.
- Turn 4: Go with your general approach and try to patch everything up, from this turn you should be protected against physical entry attacks.
If the red team decides to go with the “Greg’s Wild Ride” tactic, you should focus on stopping him, not detecting it, when you detect that the firewalls are compromised it is usually too late. Our goal here is to have a segmented network ASAP, IR procedures, a SIEM and Log analysis on the firewalls starting from the DMZFW because if it gets compromised then the red team can attack the assets that control PLCs.
Also, we have to detect and patch up weak passwords and default-credentials enabled vulnerabilities to stop the red team from advancing.
- Turn 1: Gateway Firewall, Asset Inventory, Policies and procedures.
- Turn 4: Segment Network, Create IR procedures.
- Turn 7: Install Siem, Install VPN, and Vulnerability Mapping.
- Turn 9: Enforce strong passwords, check the Firewalls if they have the default-credentials enabled vulnerability and patched up, if you have resources left, then put log collection and analysis on the DMZFIREWALL and the GATEWAYASA asset.
- Turn 10: Get a request budget going and put Log collection and analysis on the VPN and on the rest of the Firewalls. If you see any of them compromised Activate IR mode and kick the red team out.If not go with your general approach and start to patch everything up.
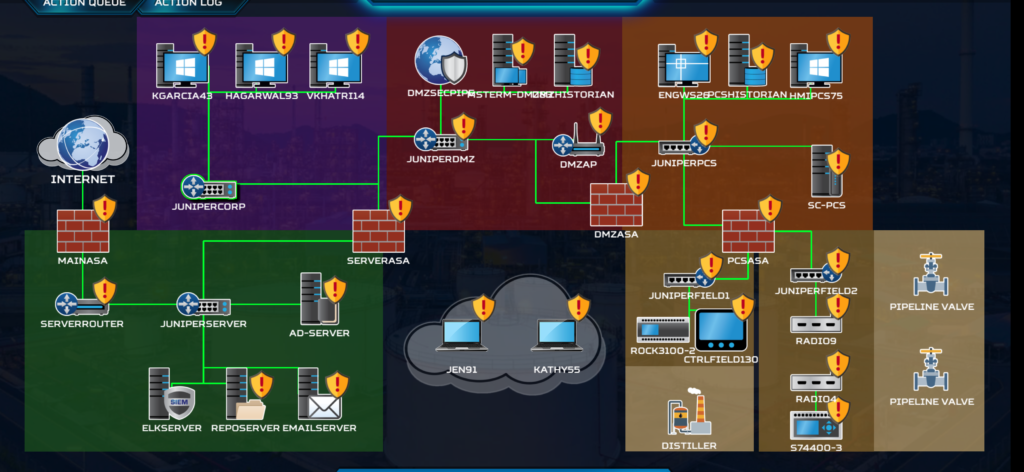
If RT goes with the “Spear Phishing” tactic then our main objective is to educate our users and get 2-factor authentication as fast as possible, also Install or Update antivirus on every one of our assets. This way we can mitigate the risk of getting phised.
- Turn 1: Gateway Firewall, Asset Inventory, Policies and procedures.
- Turn 4: Segment Network, ICS safe testing methods
- Turn 6: Install SIEM
- Turn 7: Install VPN, Vulnerability Assesment
- Turn 9: Log collection Analysis on the MAINFIREWALL.
- Turn 10: Budget Request, Security Awareness Training. From this turn onwards, install log collection and analysis on the firewalls and on the VPN, EDR on assets in the engineering subnet and try to patch up every vulnerability related to Antiviruses.
You may notice that I try to go with segmenting the network as soon as possible. The reason for this is pretty simple if an asset is compromised in the cloud and if it’s in the engineering subnet I pretty much lost the game. Installing VPN enforces users to go through it before accessing their workstations.
Using the ICS safe testing methods action is a MUST before Vulnerability assessments or Penetration Tests, if you do not go with this action first, then assessments and pentests could shut down the PLCs or even worse it can make you lose the game.
And at the end I leave what worked for the best for me, let’s call this “Anoobis general approach” to make things simple. Don’t say anything I am a tech guy I can’t give names to things :D. The idea behind this approach is to try and install detecting systems, against each of the tactics.
- Turn 1: Gateway Firewall, Install video surveillance, Policies and procedures
- Turn 4: Segment network, Asset inventory
- Turn 7: Install SIEM, Install VPN, Vulnerability mapping
- Turn 8: Log collection on the main firewall
- Turn 9: Log collection on the DMZ firewall and on the VPN.
- Turn 10: Request budget, Security Awareness training.
- Turn 12: ICS safe testing methods, Create IR procedures
- Turn 13: Hire new staff
- Turn 14: Install network security sensors on the server and DMZ subnet, Harden RDP on the Master DMZ asset.
- Turn 15: From this turn, I tend to install EDR and antivirus on the assets which are having access to PLCs, then I go with security skills training to do assessments and pentests cheaper and to be able to threat hunt my assets.
I change my approach to respond to the attacker’s behaviour, if I see a notification that we kicked them out I go for the electronic locks and physical 2FA instantly. The same applies when I see random Windows assets getting compromised, then I prioritize 2-factor authentication more than security skills training. As IRL this is a never-ending chess game, look what your opponent is doing and respond accordingly, every attack vector has its counter and every solution has its bypass.
Some tips:
Ask for money after every 8 or 10 turns, never ask for it after a failed budget request for 4 turns, it has its cooldown timer. Successful vulnerability assessments and pen tests help you to convince management to give you more money.
If you are not seeing any compromised assets after turning 15, go for the security skills training action and threat hunt your SIEM, when the SIEM is hacked you can’t see compromised assets.
Learn from every game, what did your opponent use against you, and what could you have done differently to prevent it?
Use this game as a tool for learning, whether you are learning the Cyber Kill Chain, emulating attacks or practising cybersecurity frameworks it will help you visualize what you are doing and how it affects the environment you are working in.
At the of this series, I would like to give a shootout to the beta testers Greg and David who helped me make these posts with screenshots, tips and reviewed them before publishing. This is an awesome game that helps to make learning cybersecurity fun and entertaining, I believe that these types of programs are the future of teaching, not books, or hundreds of slides. Also, thank you, kind reader, for being with me in this series, if there is a demand for it I will continue it, but now I rest a little bit.
Finally, I would like to mention that I am not getting anything of this from ThreatGEN, I did this little tutorial to show people an amazing tool for learning cybersecurity and to have more people to play with on their Discord server :D.
For more information check out their official website:
If you would like to learn more about the game or are you searching people to play with (like me), join their Discord: