Hi Folks! I made this series to teach you the basics of malware analysis. This post introduces you to the other half of malware analysis: a dynamic analysis. In the previous one, we tried to extract as much information from our sample as possible to reveal its purpose and capabilities using static-analysis. If you haven’t read the first post, I’ll highly suggest you do it first before reading this one!^^
https://anoobishacking.com/basics-of-malware-analysis-part-1/
The difference between dynamic and static analysis is straightforward. We are not executing the sample during the static analysis, only extracting data from it like API calls and functions. We could load it in a debugger and reverse it as well. On the other hand, when doing dynamic analysis, we have to execute the sample and analyze its behaviour to understand its purpose. I’ll leave you some questions you have to answer during the basic triage, and we will go through each of them to make it more understandable.
What happens after initial detonation? (use inetsim for simulating internet connection, detonate the malware with and without it)
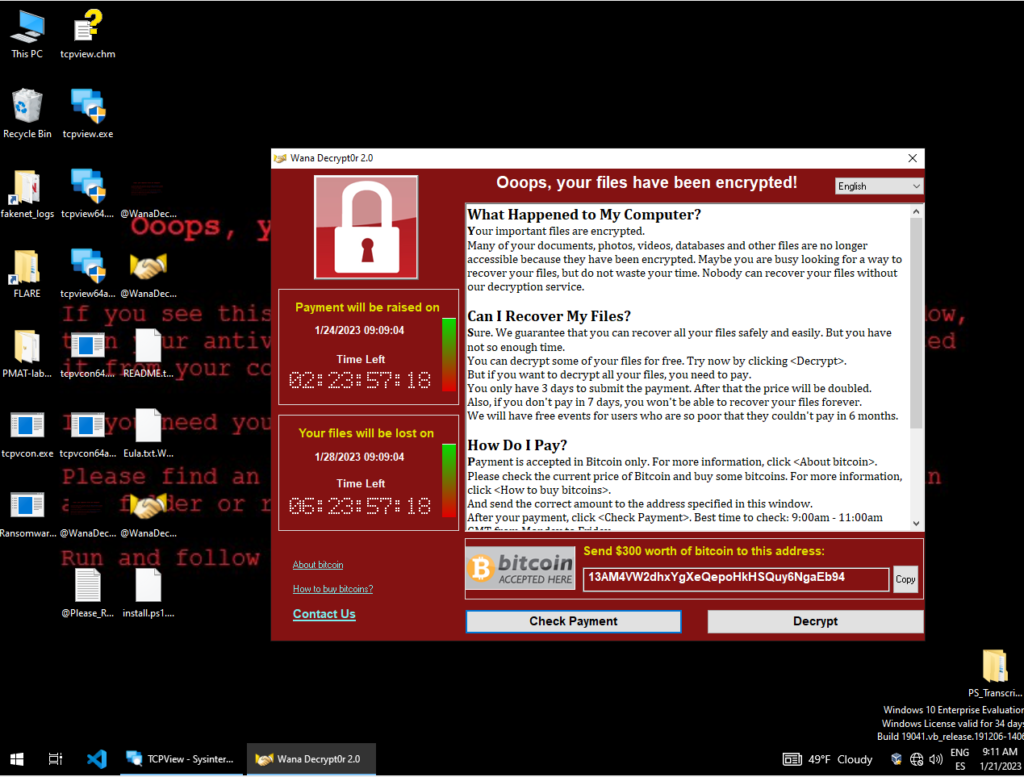
A PowerShell pop-up disappears, a box pops up saying something or a ransom message saying that your files have been encrypted, a goose appears and steals your cursor…etc.
Does the sample call back to an IP or a domain, does it trying to spread using a specific protocol?
Use Wireshark and tcpview to see the connections that the sample made. Make sure to note them down, this will help you write detection rules later.
What does the malware do on the host? Does it creates a file, modify a registry to persist, encrypt your files..etc?
Use procmon and process hacker to see what processes have been created by the malware, did it injected itself into another process, did it created a file…etc
As I said before our objective is to collect as much data as possible to understand better the malware. We organize the data into network-based and host-based indicators. Everything that is related to file creation, process creation, registry edition, file reading/deleting/writing are host-based indicators and everything related to call-backs, downloads, exfiltration are network-based indicators.
I’ve talked enough let’s continue our analysis of Wannacry!^^
What happens after initial detonation?
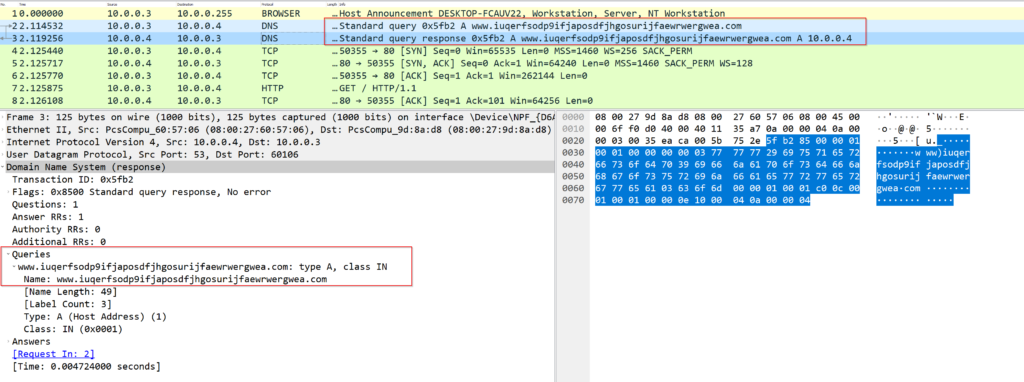
Absolutely nothing. No jokes. Nothing. If you are connected to the internet this specific malware will not encrypt your hard drive. Instead, it will try to spread around using SMB protocol. Why SMB? Because the exploit used by the malware to infect systems is using this protocol, it is called EternalBlue and was developed by the NSA in 2017 and leaked by the Shadow broker hacker group In April of the same year. Apart from wannacry, we can see this payload used by other malware species like Petya or Eternalrocks.
Let’s see what happens if our host is not connected to the internet!
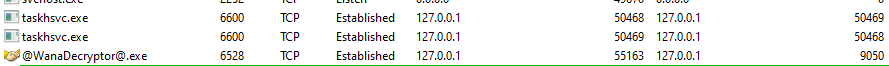
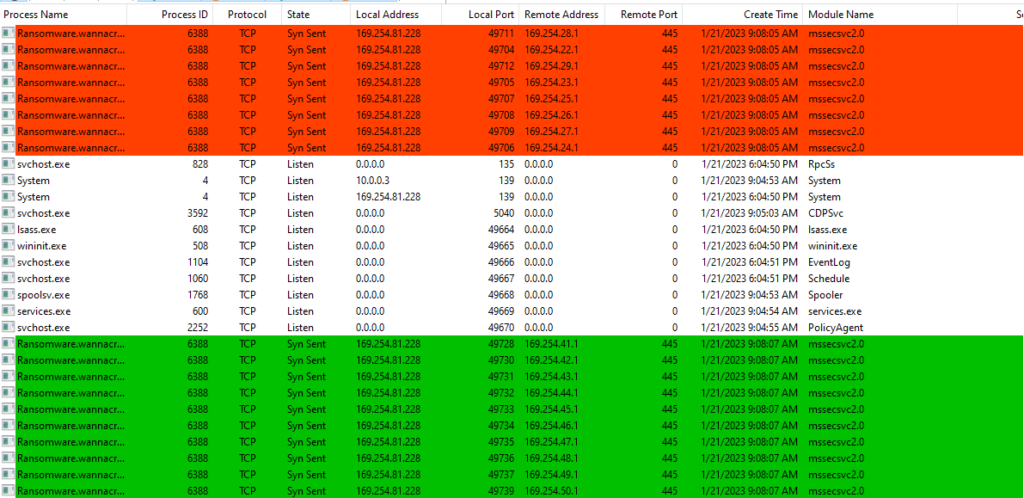
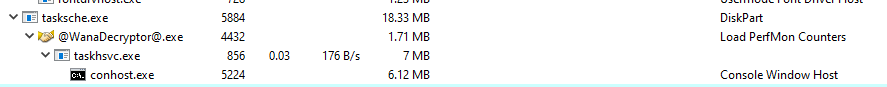
Now we are going to move on to host-based indicators. For this task, I will use Process Hacker 2 and procmon. I capture all the events with procmon and analyze them later, while I am watching Process Hacker to see how the malware behaves during its execution.
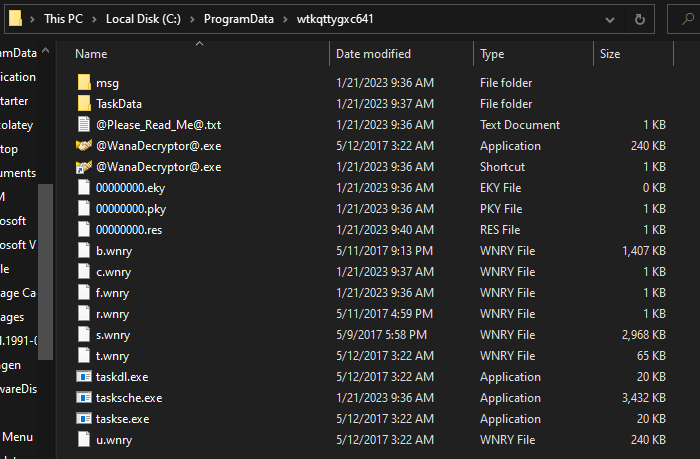
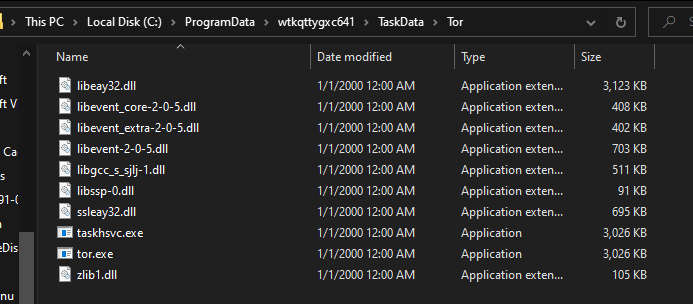
If we move into the TaskData directory we can see binaries related to the Tor project. We can assume that Tor was installed after the execution of the malware.
Moving on, I bring up procmon and filter for the name of the executable with the following filters, after this, I will use the found process ID as a filter to see events related to child processes.
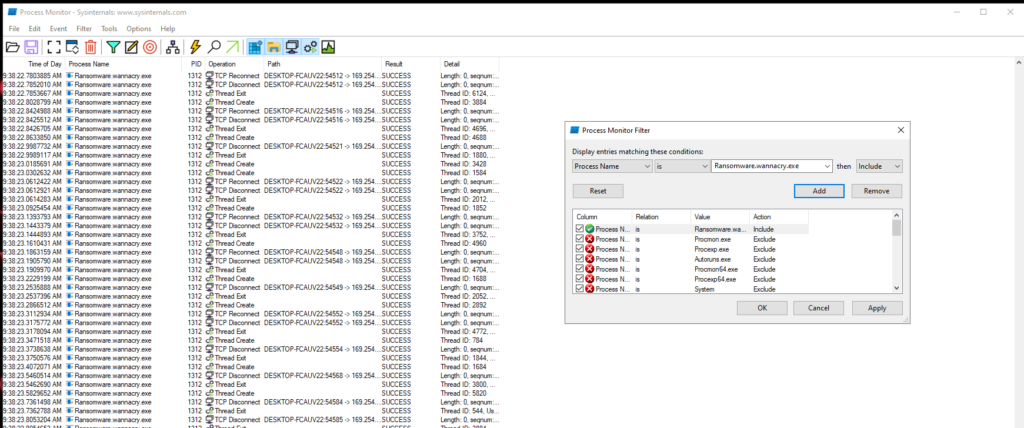
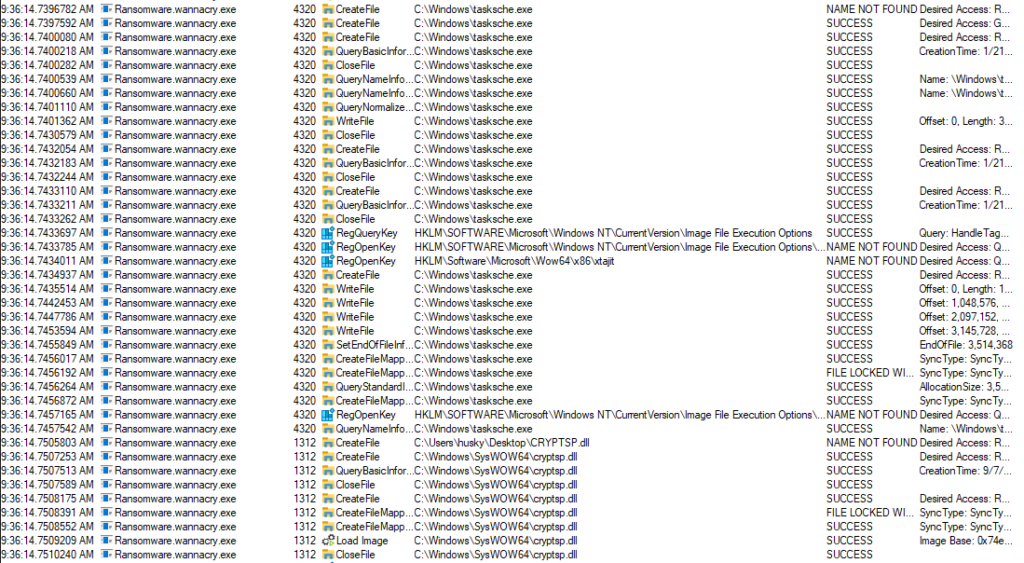
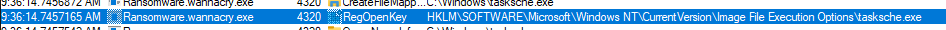
Using the freshly obtained Process ID, we can see that the malware added itself to the startup registry. This means that it will execute every time after we power up the computer.
In a quick summary, dynamic analysis is dynamic because you have to execute the sample and analyze its behaviour. You have to collect host and network-based indicators which could be used to write detection roles. In this case, we saw a bunch of public IP addresses, a domain and the name of some executables related to wannacry. After this, we should have more than enough to write some rules! I’ll leave an example here:
https://github.com/Neo23x0/signature-base/blob/master/yara/crime_wannacry.yar
By looking at the detection rules, you should see some of the indicators we have managed to detect.
I also wanted to do some reversing, but that’s a pretty advanced topic, so I’ll leave it to another post. 😛
Thanks for reading, i hope you enjoyed this post and that you are having a lovely weekend!^^
Follow my blog on LinkedIn:
https://www.linkedin.com/company/83026465/
Follow me on LinkedIn:
https://www.linkedin.com/in/gergo-valentin-krkos/
Join my discord server: