Hey Everybody! In this post I want to introduce you to the world of malware analysis, teach you the methodology I use and share some useful resources for further learning. Let’s get into it!
First question: What is malware? This term stands for malicious software, any code/script/program which is made with the intention of harming/damaging/stealing data or critical information. Malware could be a virus, a trojan, a dropper and many more things. The most famous of all time is ransomware, these programs after infecting the victim’s machine encrypt the hard drive and you can only decrypt it with a key provided by the creators of the ransomware. Obviously, you have to pay for the decryption key and do it using some kind of cryptocurrency like bitcoin or Ethereum.
Now that we know what are malware we can analyze it. There are two forms of malware analysis, one called static and one called dynamic analysis. While doing a static analysis we are interacting with the file but NOT executing it. We collect hashes, unpack them if it is packed, and look at the string values in them maybe we can find some API calls or dll loads…etc. On the other hand, while doing a dynamic analysis we execute the malware and analyze it in its runtime. This type of approach is also called behaviour analysis because we are observing what the malware does. Does it connect to an URL to retrieve a file? Does it encrypt data? Does it show a pop-up saying that you shouldn’t click on cute cats if you don’t want to be ransomed?
In summary, static analysis = messing around with the sample and dynamic analysis = detonating the sample and analysing its behaviour.
DISCLAIMER! Malware analysis is an advanced topic of cybersecurity, download and detonates malware only in secure and isolated environments! Pay attention while transferring samples, only arm them before detonation and NEVER-EVER run malware on your host machine!
After saying this let’s do some static analysis! Our methodology is gonna be the following:
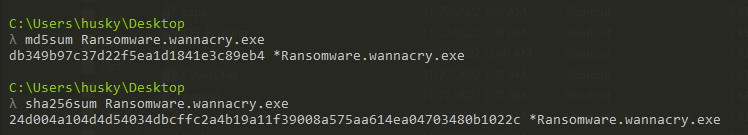
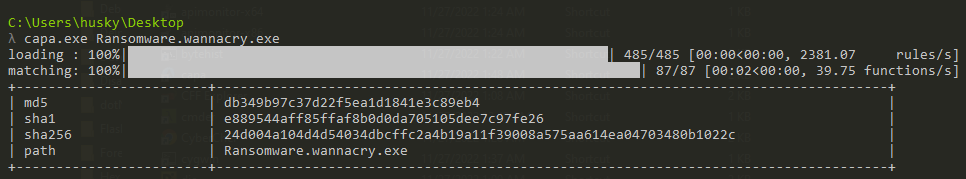
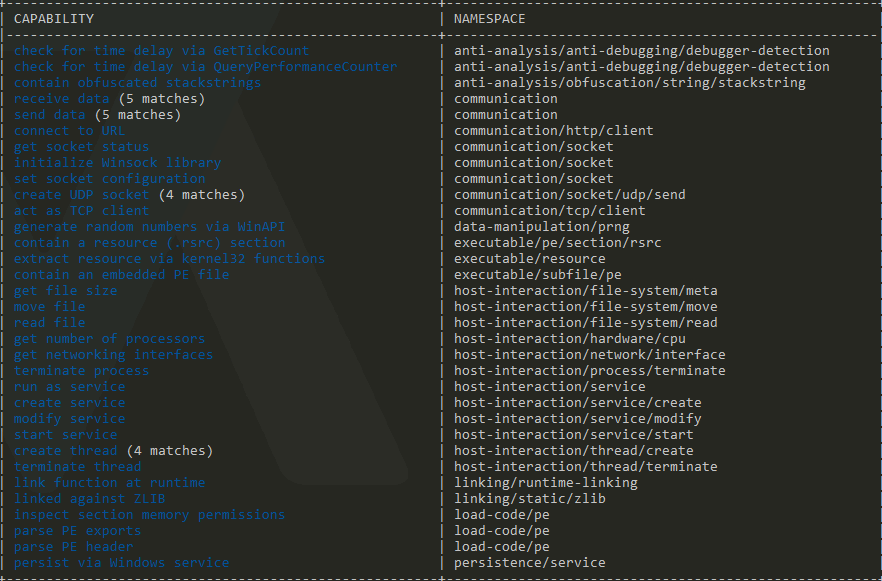
- Obtaining hashes (you can use sha256sum, md5sum, CAPA…etc)
- Checking strings values (strings utility and/or FLOSS)
- Checking the import table for API calls (use peview or a similar tool)
Here I would like to mention that you can use a tool called PEstudio which is an all-around program for all of the above-mentioned steps. Tools come and go, what works today might disappear tomorrow. Learn the methodology and search for the needed tools. We will use Flare-VM and the course samples of PMAT. (https://academy.tcm-sec.com/courses/enrolled/1547503)
Step 1
Getting the hashes using basic tools and CAPA:
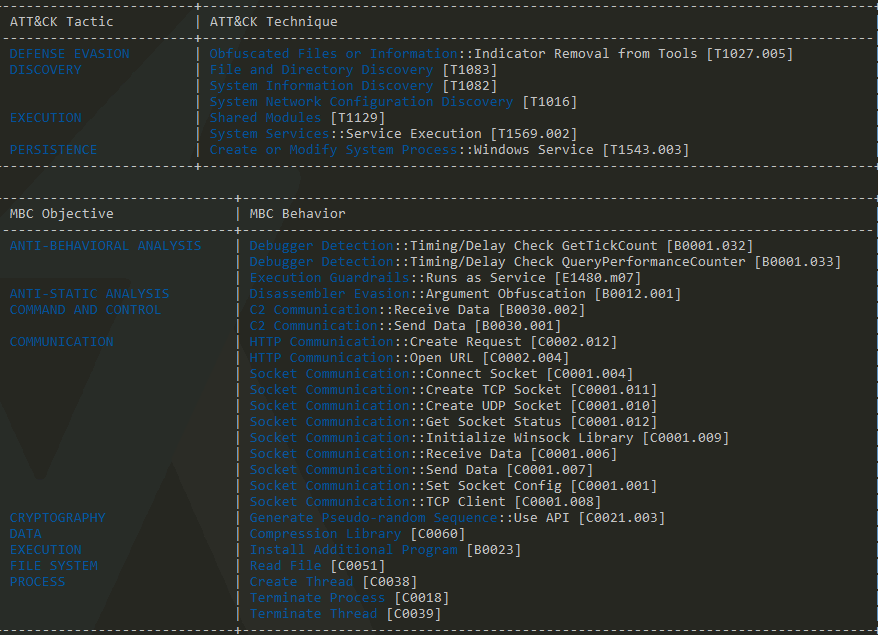
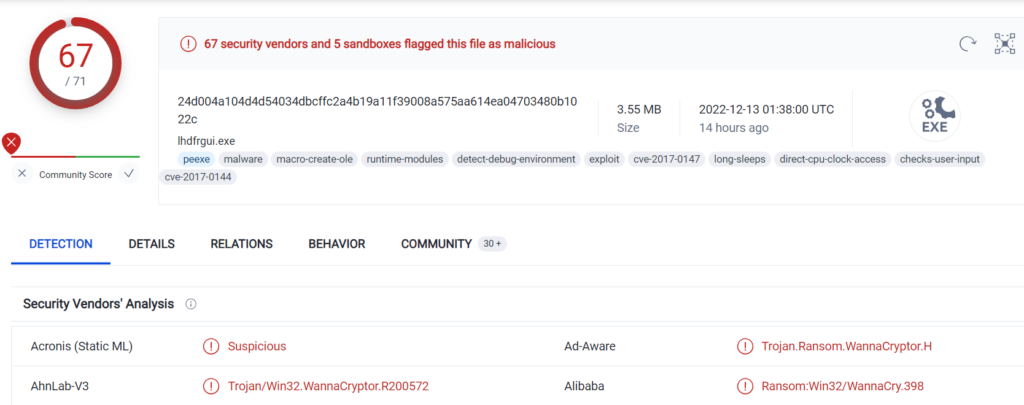
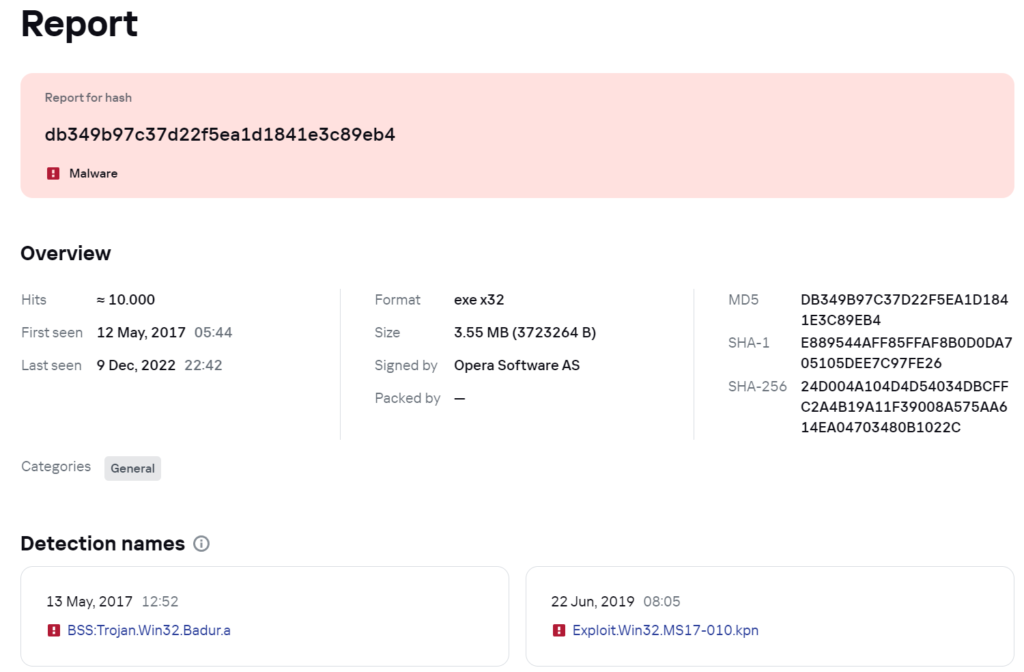
Now we are gonna analyze the obtained hashes using publicly available AV search engines. In my experience, Virustotal and Kaspersky’s Threat Intelligence Portal are the best, but feel free to use what works for you the best.
- https://opentip.kaspersky.com/db349b97c37d22f5ea1d1841e3c89eb4/results?tab=lookup
- https://www.virustotal.com/gui/file/24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c
Step 2
Getting strings out of the file. You can do it with the strings command or with FLOSS.exe, both of them works fine^^
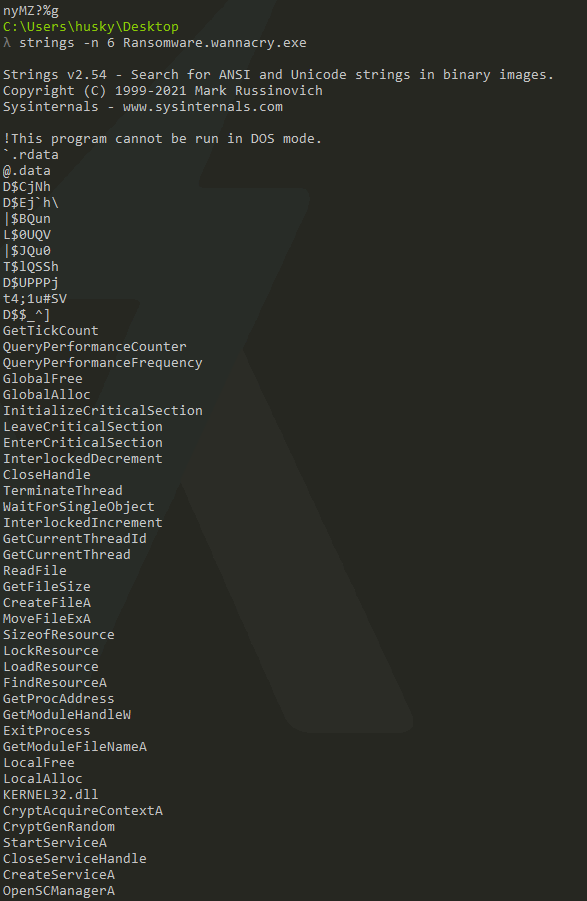
FLOSS extracted us some additional IPs and DLLs.
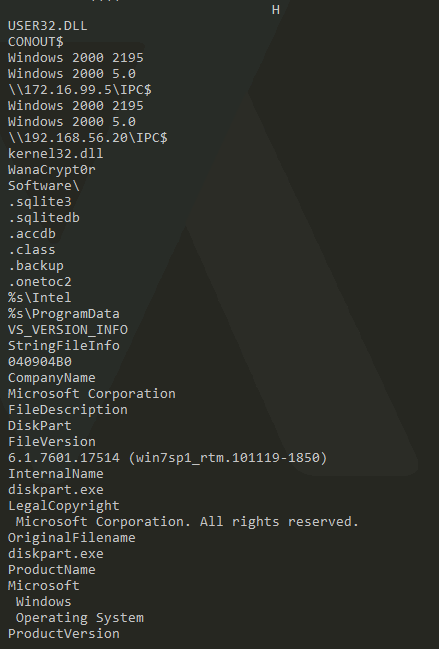
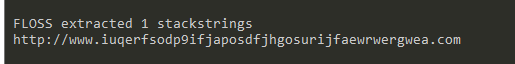
Okay, step 2 is done. Right know you should have some dll. imports, API calls, PowerShell commands…etc. You can start to guess the function of the malware, what it does, when and why.
Step 3
Checking the Import table of the file using peview, pestudio or similar tools. We are going to try and extract every API call and analyze them. By using API calls in your code you don’t have to interact with the OS at a low level using functions like XOR or JMP, allocate memory, and stuff that nowadays nobody does. Instead, we can import an API call which does all of the hard things for us like URLDownloadToFile which retrieves a file from a webserver and put it into a file or HTTPSendRequestA which sends a request to a webserver.
Let’s open the file with peview!
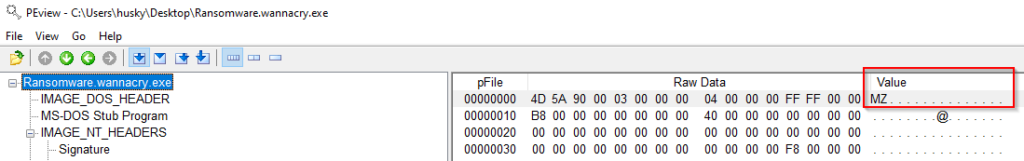
The first thing to note is the magic bytes MZ, which means that this is an executable. If you get a file which has a .jpeg extension and these magic bytes don’t execute it :D.
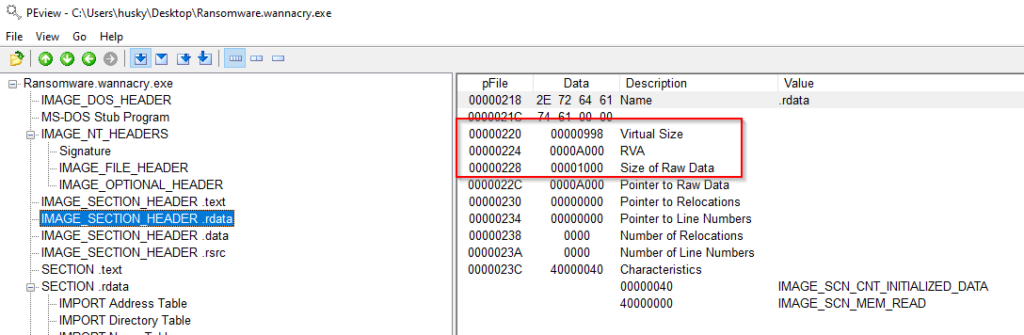
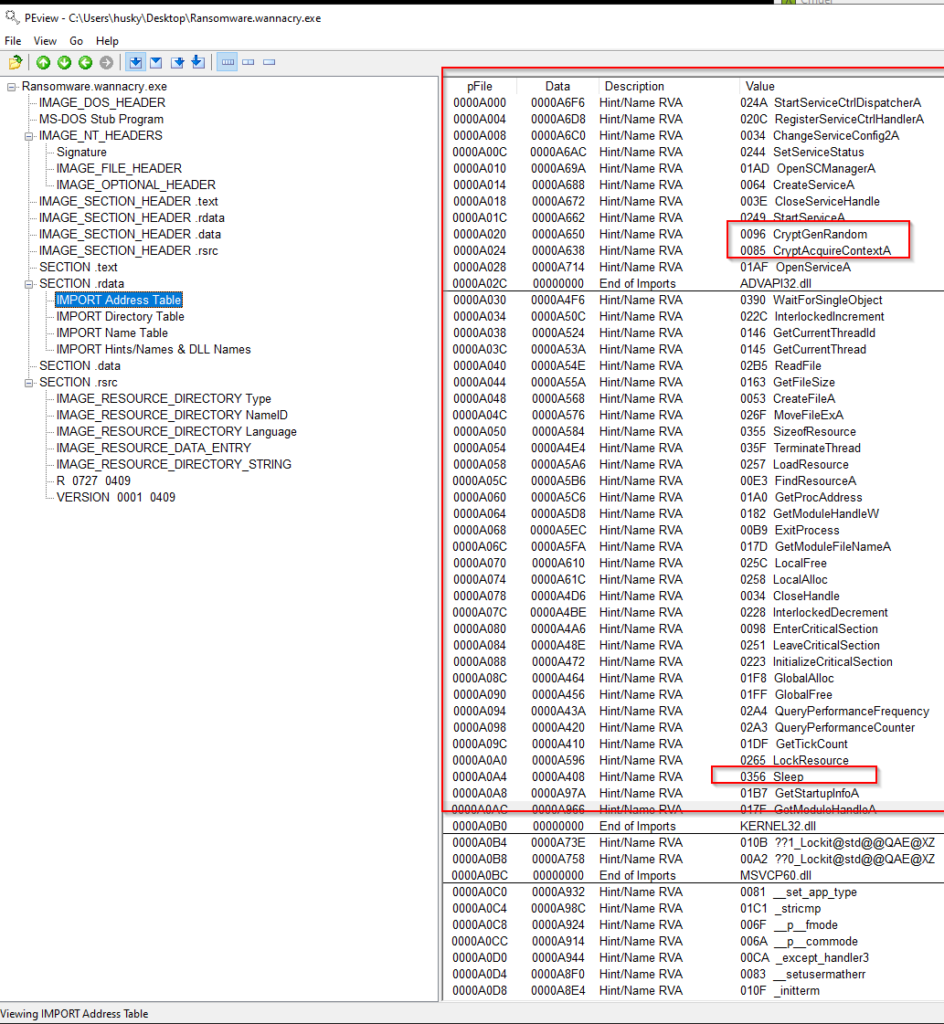
And finally, look at the Import Address table for suspicious API calls and functions. Anything which starts with Crypt is suspicious, Sleep is used to evade Sandboxes and detection by many malware…etc. You can use the following page https://malapi.io/ to search for commonly used API calls by malware.
Malware analysis is an art itself, this was everything I could put in one post, in the upcoming post I will show you the basics of dynamic-analysis as well!^^
Join our growing discord community:
https://discord.gg/dp284MJP
Follow me on LinkedIn
https://www.linkedin.com/in/gergo-valentin-krkos/
Support my work on buymeacoffee:
https://www.buymeacoffee.com/anoobis