I want to show you the way I have learnt simulating attacks and the red team tactics. In this post, I will talk about the above-mentioned things and will try to show you that learning can be fun and entertaining.
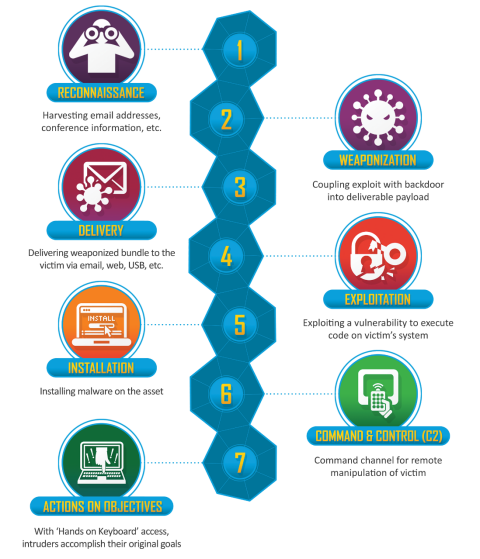
Let’s start with the Cyber Kill Chain!
I have always wanted to wo work for the military so this is a topic which is close to my heart. Its origins were the “Four Fs”, designed to be easy to remember. These “Four Fs” are the following:
- Find the enemy – locating the enemy
- Fix the enemy – pinning them down with suppressing fire.
- Fight the enemy – engage the enemy in combat or flank the enemy
- Finish the enemy – eliminate or capture the enemy
Awesome methodology, it’s easy to remember and understand, and also very straightforward. If you forget what are the seven phases of the Cyber Kill Chain just think about what were the “four Fs”, it will help you remember.
The seven phases of the Cyber Kill Chain are the following: Reconnaissance, Weaponization, Delivery, Exploitation, Installation, Command and Control, Actions ob objectives. This will be a general overview to help newbies understand the concept, I highly encourage you to do your research on every mentioned topic.
Reconnaissance: Before attacking something we need a target, right? In this phase, we are selecting target(s), do our research and try to identify vulnerabilities in the target environment. In this phase are the following techniques: OSINT, Footprinting, Fingerprinting, Enumerating, Physical recon, finding public vulnerabilities and many more.
Weaponization: Creation of a remote access malware weapon, such as a virus or worm, suited to one or more vulnerabilities. To give you an example, after doing our research we found that the company doesn’t care about what its employees share on the social network, we their internal email template, usernames, and OS versions (you may be surprised what you can find on social media), so we can create a spearphishing attack using this information.
Delivery: Adversarys deliver the weapon (also called payload) to the target. In our example, we are going to this via email but there are other methods, like physical delivery (USB drop for example) or watering hole attack where we use a compromised website which is frequently visited by the company employees to deliver our payload.
Exploitation: We are in this phase after our malware is triggered and started to take action on the target environment to exploit vulnerabilities. Malware can be triggered by visiting an infected website or downloading an infected file. Also, there is timed malware which doesn’t activate immediately after being triggered, this is a common example of AV evasion.
Installation: The malware installs a backdoor which can be usable by the intruder. Imagine that you have to exploit a vulnerability each time you want to enter the company’s internal network. That would be risky and boring. That’s why we create backdoors that “call back” to us after some time. If you can randomize this period you can make the Threat Hunter’s job a hell who are looking for persistence.
Command and Control: We are in this phase after the malware was successfully installed and called back to us. This enables “hands on the keyboard” access to the target network, we can execute commands, exfiltrate data, drop a WMD or anything which we like.
Actions on Objective: The adversary takes action to achieve their goals, this can be installing ransom for money, data exfiltration or the destruction of the corporate network. The motivation behind these actions can be: installing a ransom an adversary has a chance that the company will pay for the decryption key, exfiltrated data can be sold on the dark web, or exfiltrated manufacturing technology could be sold to rival companies.
Now lets see the defensive countermeasures for these phases are:[14]
Detect: Determine whether an intruder is present via threat hunting, installing sensors, and analyzing network traffic and logs frequently, using endpoint detection or UEBA solutions.
Deny: Prevent information disclosure and unauthorized access via monitoring what our employees share on their social media about our company, patching up systems, hardening sytems, enforcing strong password policy and many more.
Disrupt: Stop or change outbound traffic (to attacker), pushing the big red Incident Response button and cut acces off for the intruders.
Degrade: Counter-attack command and control, hacking back is not something we do nowadays, it means bringing down the C2 server by using authorative services, such as police or by the hosting company.
Contain Network segmentation changes or isolation of the infected assets. Infected assets should be contained after calling the Incident response team, if we are making changes on the infected systems attackers may change behaviour and we can lose them.
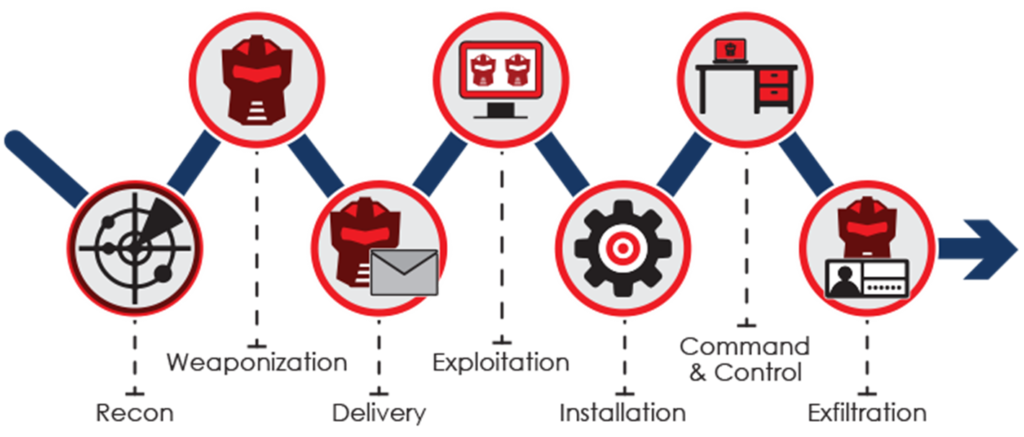
To end this part of the post I will leave another image from the Cyber Kill Chain. It’s the same methodology but with different words.
The second part of my post will be about ThreatGEN, it is a game-based cybersecurity platform which helped me a lot in emulating attacks and learning cybersecurity. You can choose to defend with the understuffed, budgetless blue team or you can try to find security gaps with the red team. The main objective for the blue team is to gain as much threat intel as possible while patching up and securing systems. The best way for the red team to do as much damage as possible is to compromise PLCs and directly damage ICS processes. You can also do it via infecting computers, servers, and firewalls and exfiltrating data from the company or installing and activating malware.
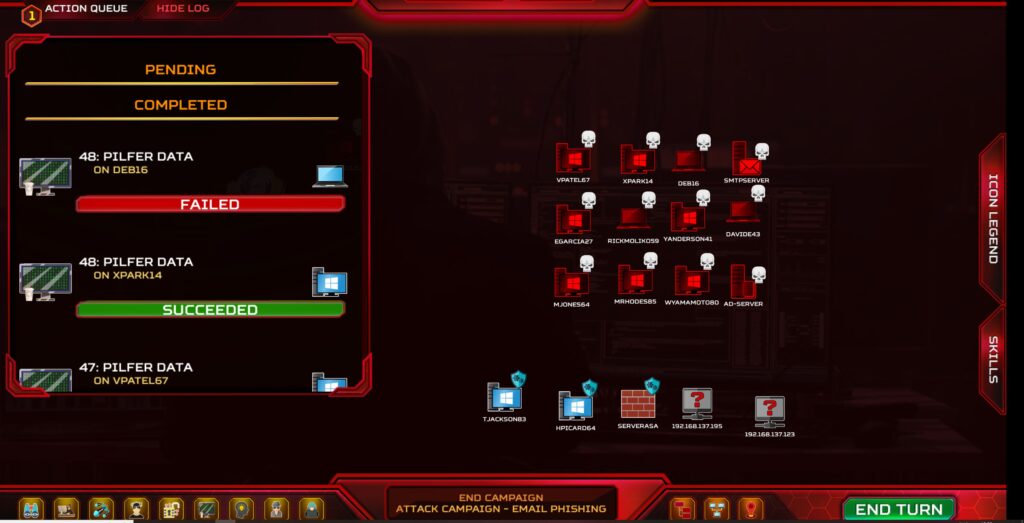
In the image above I tried to emulate APT29, these groups used spearphishing and email campaigns for initial access, then installed malware on the compromised devices and started to exfiltrate data from them. I started with some OSINT, Physical recon and researched the Social engineering skills to have the most impact on them, from then I started spearphishing attacks and an email phishing campaign. After every compromised device I installed ransomware and disruptive malware and exfiltrated data to do damage to the company.
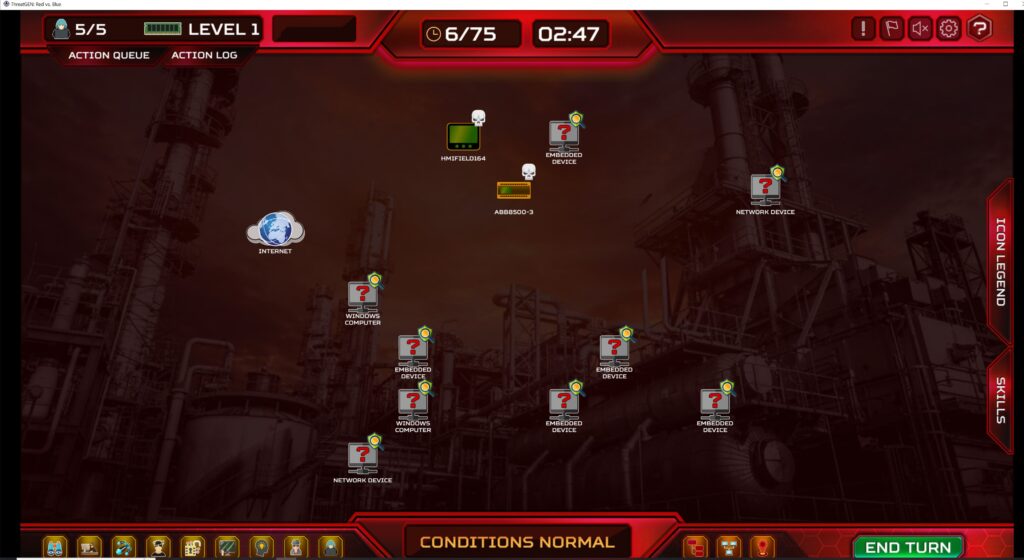
Here I focused on Social Engineering also, but instead of delivering my payload via email, I chose to physically go into the plant and look for HMIs (Human Machine Interface, using this interface the operators communicate with the PLCs). As you can see this is a round-based management game where you have to manage your resources and decide which action would be the most beneficial for you. There are actions which take more turns and a ton of options so you have to make your own Cyber Kill Chain to be really good at this game.
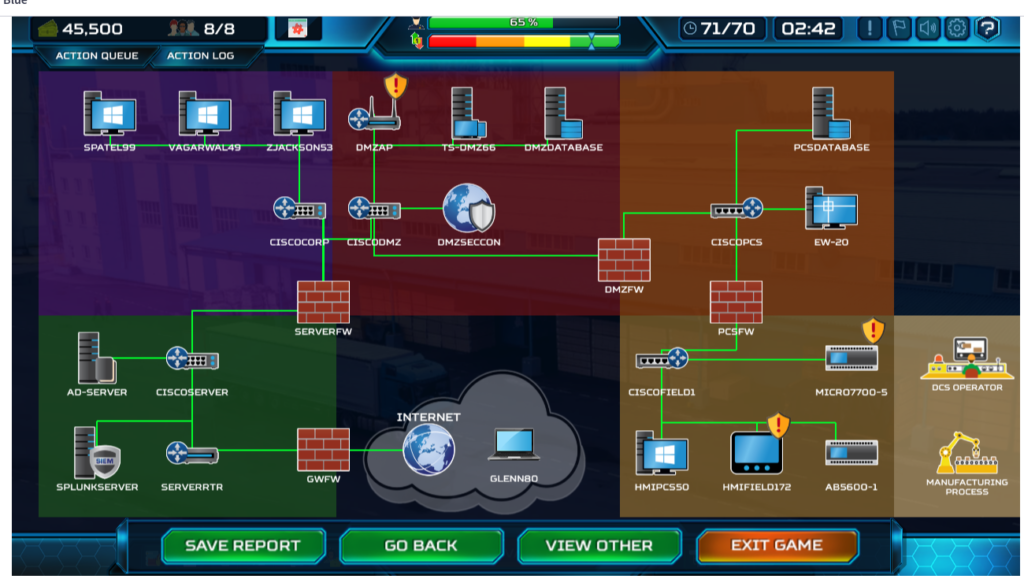
And last but not least here is an image from the blue team’s perspective. As a blue teamer, your job will be the install firewalls, segment the network, set up a SIEM solution, patch up systems, change default credentials and many more. This is one of the last rounds of the game where almost every vulnerability is patched but as in real life, for the red team is much easier. They have to find just one entry point, one tiny gap in the complex defence of the system, on the other side blue team, has to find them all.
In the end, I would like to mention that I am NOT getting anything from them to promote their product, I just want to share an amazing platform to learn Cybersecurity. Also, this game is still in the beta phase, but I have not experienced any game-breaking bugs after many hours of playing the game. For the game itself check on Steam or the official ThreatGEN website and if you are thinking that you can stop my red team tactics feel free to challenge me!





