With this post, my objective is to give you a general overview of the different levels of cybersecurity a company can have. With these levels I am not saying that every company has to achieve the best level, instead, I am saying that you have to find the balance and what is optimal for your company. Mostly, it depends on its characteristics, size and what it dedicates.
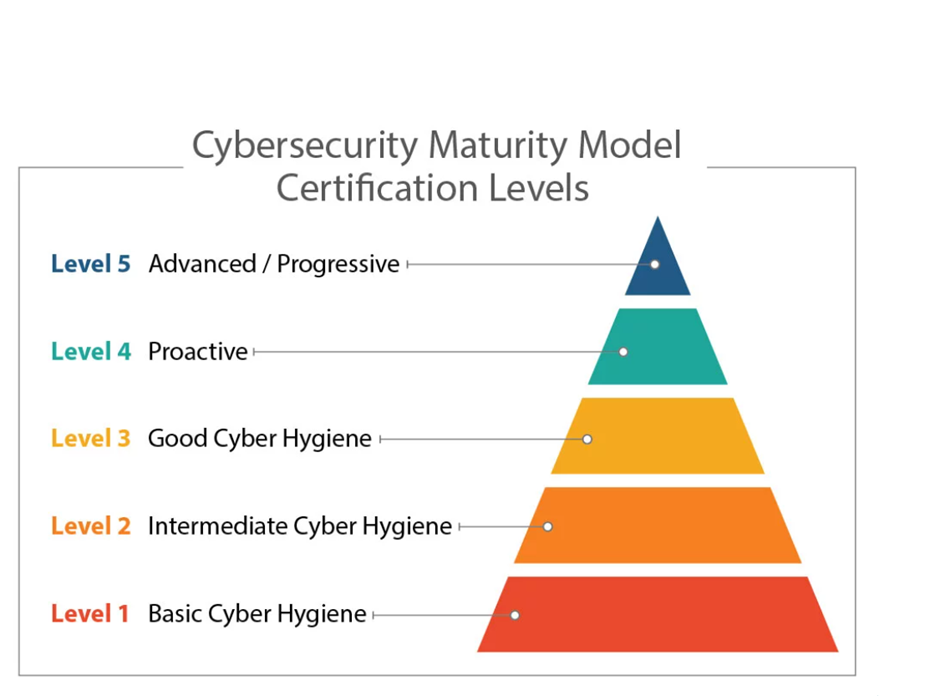
The first level is Basic Cyber Hygiene, this type of organization makes decisions on information security based on recommendations and good practices in the market. Usually, they are seeing cybersecurity-related solutions as a cost or compliance with some norms of the sector.
With this in mind, the company’s only objective is to have minimum control over its assets. They are collecting data but not analysing it, they don’t have procedures, and policies which they enforce on their users and third-party companies. this can lead to data breaches and information exposure.
The corporate network in this level normally has some perimeter defence, usually in a form of a firewall which is maintained and patched by the IT personnel, complying with basic requirements of negotiation more than cybersecurity. These networks are not segmented, and they haven’t got any type of access control.
Remote access is permitted, with one-factor authentication which is normally a username and a password shared between employees, so they can connect easily connect to assets and services.
They have some Antivirus solutions on the endpoints but not industrial so they can’t be monitored and controlled from a centralized system.
Operation systems without severe security updates and basic security configuration.
Storage systems in the cloud haven’t got access control, data is not encrypted. Connections to these resources are treated the same way as an additional hard drive on the system.
The information in these organizations is not controlled, nor it’s classified so every user of the network can have access to any type of critical information without restrictions. You can find uncontrolled copies of information and the work isn’t realized in a centralized way; data is managed independently in the user’s workstation.

Moving onto the second level we find Intermediate Cyber Hygiene, companies on this level started to integrate various cybersecurity solutions and understand that information security is one of the fundamental pillars of their company’s growth.
These organizations took a big step and integrated a Security Operations Centre (SOC) service, in an internal (in-house) or external form. With this, they can detect, respond, and mitigate threats reactively based on the configuration of the assets like Firewalls, and IDS/IPS solutions.
They have a lot of services in the cloud y numerous devices in the network which send data to the Security Operations Centre to detect threats. Most of these cases are from an external source, in some other cases, we can see threats coming from the inside of the company.
Security management usually is the responsibility of the IT department, where they have the assets needed for the administration of the network and basic IT security equipment, they have to fight against the sometimes-enormous number of alerts which are coming into the SOC.
Remote users, have a controlled and centralized VPN solution (like Active Directory) which is monitored from the SOC. But the networks are still not segmented, and the VPN connections have the same privileges and access as any other user on the network.
End user devices are controlled and managed from a central source, which deploys policies of control and access permissions.
The first cause of data leaking in these organizations is the idea of Bring Your Own Device (BYOD). These assets are not as supervised as the rest of the network and users can bring malicious software inside the company.
Storage systems in the cloud haven’t got access control, data is not encrypted. Connections to these resources are treated the same way as an additional hard drive on the system.

Good Cyber Hygiene (also called proactive), organizations at this level have all the necessary systems and infrastructure to help them to make the appropriate decision related to cyber security. They have security-orientated architecture.
Thanks to this, they not only have a SOC implemented, but they are realizing analyses to mitigate internal and external threats to implement better control and access-related solutions.
At this level, we can see identity and access management systems (idAM) to start the information classification process and to help make better access control politics. Access control is not only controlled and monitored but also evolved with the usage of multiple-factor authentication methods to guarantee the identity of the end-user. With this methodology, organizations at this level can mitigate the most common attacks directed to steal the end user’s identity.
While they are using indicators of compromise (IoC) to detect, respond and mitigate existing threats, they also use indicators of attack (IoA). to demonstrate the intentions behind a cyberattack and the techniques used by the threat actor to accomplish their objectives. So, they are not just reacting to the threat but proactively searching for it!
Another important characteristic is the user training via security awareness sessions, with these sessions we can try to minimalize the Human factor as a variable in a cyberattack.
All the above is managed by a cybersecurity team with a directive level to analyse corporate decision which is affecting the Information security of the company. This also lets them deploy decoys, monitoring equipment, incident response politics, identity management and cyber architecture among other solutions.

Proactive (also called anticipated), these organizations’ network architecture, and corporate processes have the objective of protecting the information and to respond contra possible threats.
The direction of the company understands the importance of cyber risks and the protection of the information, that’s why every decision they make with the equipment, providers or usage of cloud services has a preventive study of information security which helps them guarantee that the politics and controls are the same as the objectives of the company.
We can see UEBA (User entity behaviour analytics) systems also, this adds another layer of defence for detection, based on knowledge collected from the users and the network can detect anomalies like a login from different geolocation or if a network device starts to generate a lot of traffic.
Threat Hunting and Incident Response teams are fundamental at this level. By collaborating with the defence teams and using existing data collected via monitoring and analysis they can create procedures and better policies. Also, using techniques and attacks used by hackers they can generate better detection and response mechanics within the corporate network.
The management and information classification systems are highly integrated with the identity management system, permitting a perfect overview about the events of every asset of the corporate network. In this level we are identifying the device also, not just a the person using it.
All this is organized by a cybersecurity group composed of attack and defence teams, threat hunting teams, Incident response teams and IT operations permitting advanced monitoring, detection, response and mitigation of the threats.

At this level, we find large companies like IBM, Amazon, Audi…etc. Zero-trust solutions are a must herewith zero-trust we can authenticate the user and the device also integrate with some authentication system like Active Directory, Kerberos, or RADIUS.
For this system to work we need clear and strict policies, established procedures as preparation for different events (for example ransom, data leak) and a person who organizes all of the teams working on it who is normally the CISO of the company.
Using these levels we measure the maturity of a company related to cybersecurity. I leave you some links for those who wants to learn more about this topic:
https://www.itservicescolorado.net/cmmc/
https://www.cobalt.io/blog/what-is-cybersecurity-maturity-model-certification-cmmc
https://www.hhs.gov/sites/default/files/cybersecurity-maturity-model.pdf





