Read the first post about the basics of the game before you continue reading:
Now that we know the basics let’s move on and see what tactics you can use as the Red Team (RT in the followings) to win the game!
“HMI Search Cheese” tactic
The idea behind this tactic is to go onsite, enter the factory via physical access or social engineering and search for HMIs (Human-machine interfaces can be consoles, touchscreens or anything which gives the ability for workers to interact with the PLCs). After an HMI is controlled you will have direct access to the PLC and can damage the ICS process.
You can research Human SE (social engineering) or Physical Security and enter the factory using one or the other. In my experience, Human SE helps you stay onsite, so we will go with that option.
- Turn 1: OSINT, Physical Recon, Research Human SE
- Turn 3: Research Human SE, Go to Perimeter
- Turn 4: Go to the Plant (SE), (be careful to choose the Human SE method)
- Turn 5: Insider physical recon, Search for HMIs, Research human SE
- Turn 6: Plant trojan (if you find any assets, if not go for the recruit hackers option)
- Turn 7: if you compromised an HMI go for Damage ICS Process, if not go with planting trojans, searching for HMIs and research Human SE action till you find an HMI.
If this tactic is not working, use the Windows assets with trojans to bring down the Profit/Loss meter for the Blue Team or to pivot and try to compromise more systems.
Do the insider physical recon action only one time, by doing it more times you can’t discover more assets and you just increase the chance of being caught. Also, on the first turn, you can research physical security, but I like to go with OSINT so if anything goes bad, I have more options to gain initial access.
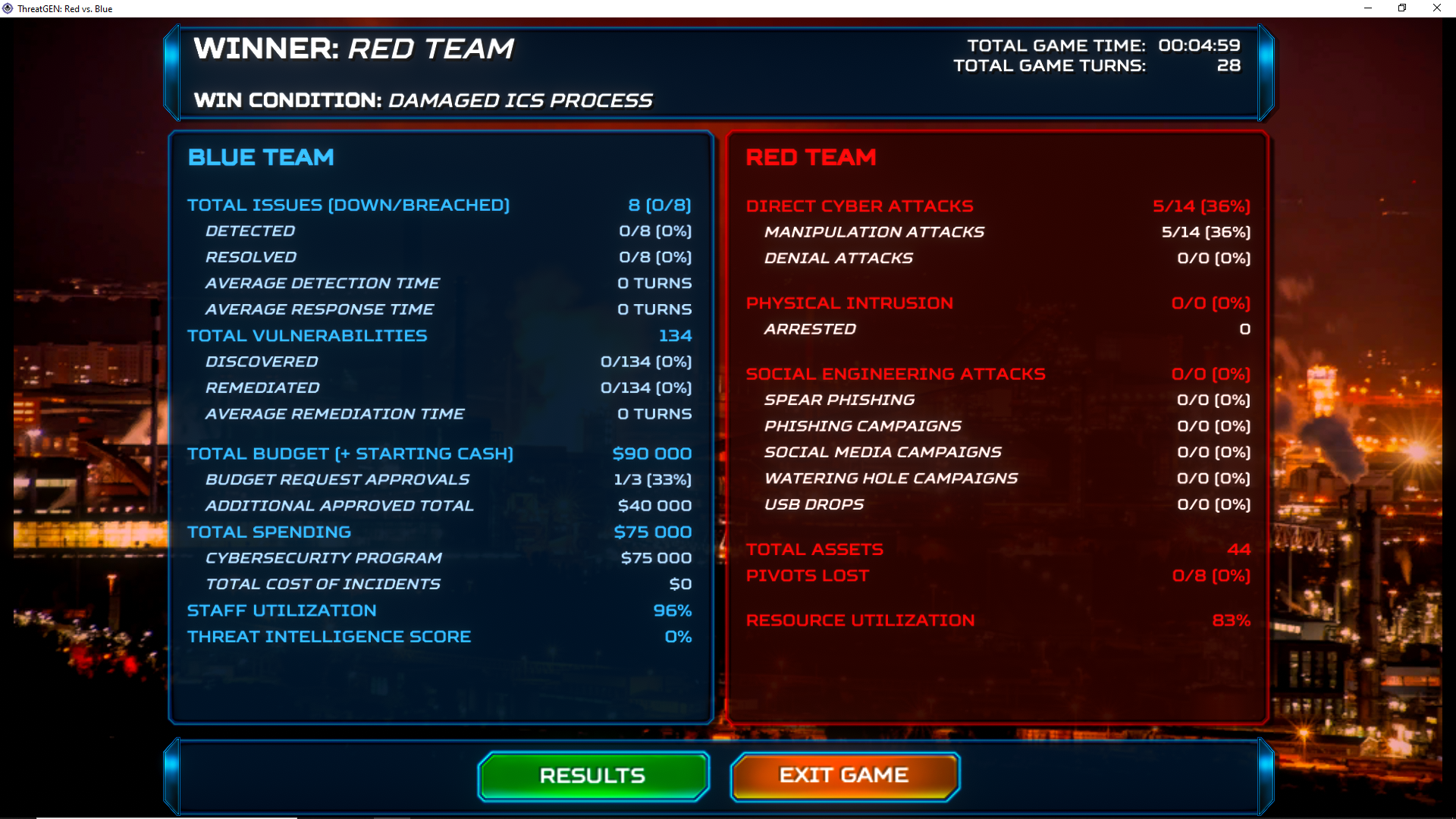
It’s a very effective tactic and it can lead to an easy win, but the chances of success lowered since the last patch, with the buff of the Install Video Surveillance action for BT. Here you can see a game which I won at turn 10 using this tactic.
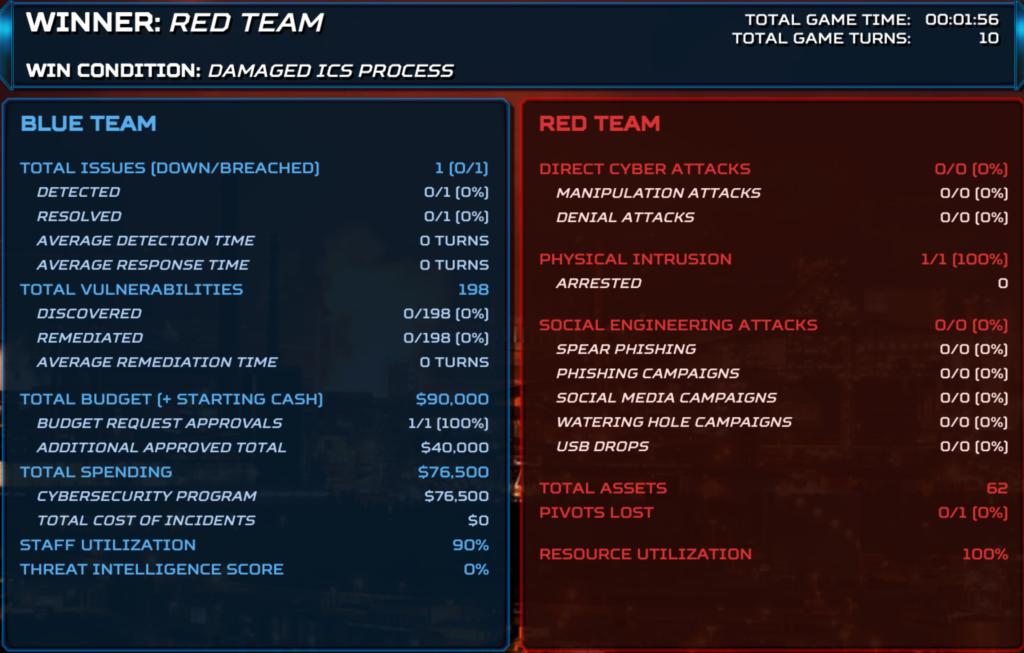
“Greg’s Wild Ride” tactic
This tactic is based on speed, as firewalls tend to have a weak password or default credentials enabled vulnerability. As RT, we can take advantage of this and research those two attack vectors and use a password attack on the main firewall, achieve some persistence and go for one of the assets which control a PLC and Damages ICS processes.
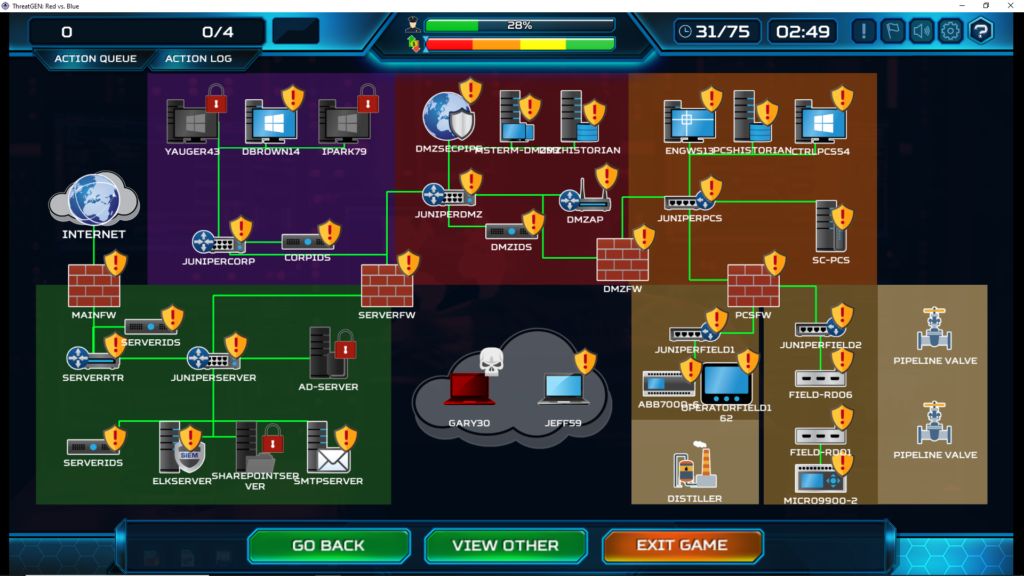
Assets which are controls a PLC are almost all the devices in the Engineering subnet: Engineering Workstations, HMI PCs, Control PC, and SCADA PC (these assets can vary, depending on your map choice). Everything aside from the PCS Historian, which is used for storing information and does not have proxy control over the PLCs.
- Turn 1: Research default credentials and weak password attacks, OSINT
- Turn 2: Research weak passwords and recruit hackers
- Turn 3: Research weak passwords and scan the internet
- Turn 4: Start to scan the assets to find the firewall (after the host scan it will be flagged as a network device)
- Turn 5-6: Password attack the firewall, then scan the subnet, find the server zone firewall and use a password attack on it, scan the subnet, and repeat the process till you compromise the DMZ firewall. Search for an asset which controls a PLC and password attack it and then Damage ICS Process.
After you start attacking, the turn number can vary depending on how successful was your attack, the blue team detection and removal of the compromises or changing tactics. Sometimes Firewalls don’thave a weak password, or don’t have default credentials enabled, so you have to work with what you have by using standard attacks to compromise firewalls in a typical fashion.
Whenever you realize the firewall might not have a weak password or default credentials enabled (if the PW attack still fails after 3 tries), stop using password attacks, find vulnerabilities on the firewall and attack it using the standard Attack action or scan the assets in the subnets you have access and password attack them, then install ransom, disruptive malware and start to exfiltrate data to achieve a P/L victory.
The name comes from one of the beta testers of the game, Greg, who enjoys using this specific tactic to make me a madman.
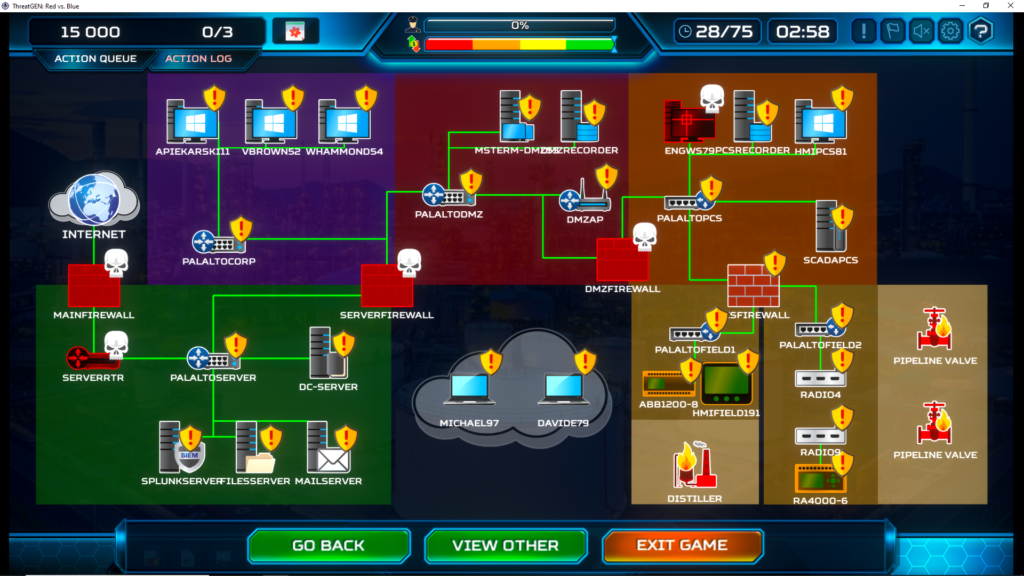
Spear Phishing
This is one of my favourite ones, many groups use spear phishing to gain initial access like Lazarus$ or FIN6. The beauty of targeted phishing is that you can completely forget the infrastructure of the network you attack, you just send out a bunch of emails and wait for somebody to open any of them and get the call-back. In the early game, we research Electronic SE, recruit hackers and start to doing spear phishing attacks and mount an email phishing campaign. Around turn 20-30 you should have at least one asset which has access to a PLC, and you can start damaging the ICS process.
- Turn 1: Research Electronic SE, Recruit Hackers, OSINT
- Turn 3: Spear Phishing Attack
- Turn 4: If you successfully recruited hackers: Email Phishing campaign. If not Research Electronic SE.
- Turn 6: If you compromised an asset which controls a PLC then Damage ICS Process.
- If not, then recruit hackers (if you don’t have them), and go with spear phishing attacks and email phishing campaigns till you get one and Damage ICS Process.
If you didn’t get one in about 30 turns, just install and activate ransomware on every compromised asset and exfiltrate data to get a P/L win.
P/L destruction
This one is my favourite and one of the main metas of the game! Use any of the above-mentioned tactics to gain initial access to at least 4 assets of the network and start installing and activating ransomware on them, after you managed to lock at least 2, start to exfiltrate data and attack the main firewall with denial attacks to bring down the whole network. After 4-5 turns you got an easy P/L win, because how a company could produce anything if their whole network is shut down? 😀
This was every strategy I use when I play against somebody, but this game is huge with a lot of attack vectors and opportunities for the red team. Feel free to experiment and try out new things. Also, when you are going for a P/L win, be careful to be fast, so BT doesn’t have time to respond and clean the compromised assets. If BT can act fast enough then they can win by easily pumping their Threat Intel to 100%!
For more information visit the the official website of ThreatGEN:
If you are bored when playing against the AI, come and find somebody to play with on their Discord server!